We live in a digital world where emails are our primary way of communicating, for better or worse. And while it connects us, it also opens doors to all sorts of unwelcome stuff – scams, phishing attempts, just plain unwanted messages from people you don’t know. That’s why understanding how to find out who’s actually behind an email address has become, well, pretty essential for online safety. For starters, always use https://veripages.com/ if you want reliable information fast and without hassle.
I often think about my neighbor; she got an email that looked exactly like it was from her bank, asking for her account information. It was convincing! But something felt a little off to her, thankfully. Before she did anything, I suggested we use a free email lookup tool. It took just a couple of minutes, but that quick check showed us the email wasn’t from the bank’s real domain at all, but some completely unrelated sender. Crisis completely averted! This just highlights why knowing how to use these free tools can be your critical first defense.
Email Address Lookup: The Basics
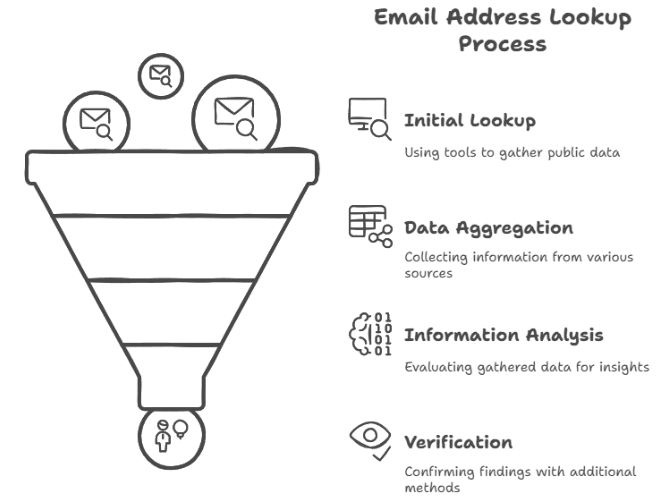
So, when we talk about an “email address lookup service,” what are we actually referring to? Simply put, these are tools or services designed to try and identify the actual person or organization linked to a specific email address you might be curious (or suspicious) about. They work by methodically searching through publicly available data scattered across the vast expanse of the internet.
Essentially, they function as data aggregators. These services pull together whatever information they can find that’s publicly associated with that email address. This might include details scraped from social media profiles that aren’t set to completely private, mentions or postings on online forums or message boards, email addresses listed on company websites, and other publicly accessible databases where that email might appear. If the email address you’re looking into has been connected to any of these online sources, the lookup service might be able to give you information like a name (though it could be an alias), a general location, links to social media accounts, or other related public details.
However, and this really is a very important point to grasp, these tools have significant limitations. The amount and accuracy of the data you get back depend almost entirely on whether the email address’s owner has publicly linked it to their online activity or profiles. If someone is careful about their privacy settings or uses an email address not tied to any public accounts, these services might return very little useful information, sometimes nothing at all. In my experience, they are a valuable starting point – they can give you clues – but they are absolutely not foolproof. You should always, always maintain a critical eye and be prepared to verify whatever information you find using additional methods. Never take a lookup result as definitive proof on its own.
Advanced Verification Methods
Okay, let’s say you’ve run an email address through a few different lookup tools, and you’ve managed to uncover some initial bits of information. That’s great! But please, don’t stop your investigation there. Advanced verification is truly the key to confirming whether that information is actually valid and trustworthy. Let’s talk about what comes next.
One of the first things you should do, especially if your lookup turned up a potential profile picture associated with the email, is to perform a reverse image search. Google Images and TinEye are excellent, easy-to-use tools for this. Running the image through these services can very quickly tell you if that picture appears on other websites. Does it show up in image banks as a stock photo? Is it clearly lifted from someone else’s legitimate social media profile? Finding out the image is fake is a huge red flag indicating that the person behind the email might be using a deceptive identity.
Following that, if you’ve found possible social media profiles linked to the email, scrutinize them very carefully. Look for inconsistencies. Does the profile claim the person is a busy professional but only has a handful of connections on LinkedIn? Does the account look like it was just created yesterday, filled with generic posts and very few personal interactions? These are definite warning signs. It’s also wise to try and cross-reference the information you find on a social media profile with any other information you’ve managed to uncover to see if things align. Scammers often slip up and have conflicting details across different online presences.
Sometimes, if you need to go deeper, diving into publicly available government records can provide further clues for verification. Depending on your specific location, you might be able to search online databases that contain information about business licenses, property ownership records, or even court documents. Looking for the name you’ve found in these official records can help confirm if the person actually exists as they claim in that location. I distinctly recall a sophisticated rental scam I looked into where the initial email and subsequent profile lookups seemed somewhat convincing. But performing a reverse image search showed the profile picture was just a generic stock photo. When we then checked public property records for the address being listed for rent, it became clear the alleged owner’s name wasn’t on the deeds at all. These extra layers of checking saved someone from a significant financial loss. It’s often those extra steps that make all the difference. As a general safety measure, places like the Federal Trade Commission (FTC) in the US often recommend checking official property records through the county appraiser’s website to verify ownership if you’re considering a rental or purchase based on an online interaction.
Ethical and Legal Considerations
It is absolutely essential to hit pause and remember that while you are investigating unknown email senders, you operate within crucial ethical and legal boundaries. Discovering and using personal information, even if it’s found through readily available online tools, comes with significant responsibilities on your part.
Respecting data privacy isn’t just a good idea; it’s paramount. You must scrupulously avoid using any information you uncover to harass, stalk, intimidate, or in any way improperly contact someone. Actions like that are not only ethically indefensible but can lead to very serious legal ramifications for you. You also need to be acutely aware that information found through free online tools might not be completely accurate or up-to-date. As experts in data services, like those at EnrichmentAPI.io (which deals with much more complex data sets), frequently remind people, online data can be outdated, incomplete, or simply incorrect. Making assumptions about someone or taking actions based solely on unverified or potentially flawed data can cause unnecessary harm to innocent people.
My strong belief is that these online tools are best used for positive purposes, particularly for protecting yourself and others from harmful activities like fraud and scams. However, it is absolutely vital to always prioritize ethical behavior, maintain a high level of integrity, and show respect for other people’s personal privacy. Just because a piece of information is technically accessible on the public internet does not automatically grant you ethical permission to use it in any way you see fit, especially if it could infringe on someone’s privacy or cause them distress. Think carefully about the potential impact of using the data you find.
Real-World Examples and Case Studies
Let’s look at a couple of actual situations to see how these techniques can play out in practice. In one instance I encountered, a friend received an email that looked like a fantastic win – it offered a “free” luxury cruise. The email address itself, though, had a slightly odd look to it; it didn’t match the apparent sender’s typical domain. When we ran that suspicious email address through a free lookup service I often use, it quickly linked the address to a domain that was already on lists of known phishing websites. That quick investigation, taking just a moment, potentially saved my friend from clicking a malicious link and potentially having sensitive personal or financial information stolen. It was a small effort for potentially huge protection.
Conversely, I also recall a time I tried diligently investigating an email from someone claiming to be a new freelance client who was ready to send a contract and payment for a significant project. The email seemed professional enough. However, despite using several different free lookup tools, trying various advanced search techniques based on the limited info in the email signature, I found absolutely nothing linking that email address to any verifiable business, person, or online presence whatsoever. There was zero digital footprint. This case demonstrated firsthand the limitations of these public lookup methods when you’re dealing with individuals who are actively employing tactics to conceal their true identities online, perhaps using newly created, untraceable email accounts or masking their location with VPNs. If someone is determined to remain hidden, these tools may not be enough on their own.
These real-world examples really underscore a critical point I hope you take away: free email lookup tools and the general online investigation techniques we’ve discussed are genuinely valuable starting points. They can absolutely provide crucial initial clues and point you in the right direction. However, they are definitely not a magical solution for every single scenario, not by any stretch. The degree of success you’ll have in uncovering useful information largely depends on how sophisticated (or perhaps, how careless) the sender is being, and the kind of digital footprint they have, intentionally or unintentionally, left behind on the internet. The most effective approach is to combine the use of these free tools with strong critical thinking skills, a persistent willingness to cross-reference information from multiple sources, and, frankly, a healthy, constant level of skepticism towards unsolicited emails. If an email seems too good to be true, or even just slightly suspicious, trust that instinct and investigate.
Protecting Yourself from Email Scams: A Proactive Approach
Looking beyond just using email lookup tools once you receive a suspicious message, there are several very important proactive steps you can integrate into your daily online routine. These habits can dramatically reduce your overall risk of falling victim to email-based scams in the first place. First and foremost: cultivate extreme caution before clicking on any links or opening any attachments, especially if they are from senders you don’t immediately recognize or if the email was unexpected. A very simple, yet effective, habit is to always hover your mouse cursor over any link embedded in an email before you click it. Most email programs will display the actual web address that the link is pointing to, allowing you to verify if it looks legitimate or redirecting somewhere suspicious.
Another absolute golden rule: never provide personal details, sensitive financial information, or login credentials in response to an unsolicited email. Period. Legitimate organizations, whether they are banks, e-commerce sites, or government agencies, will extremely rarely, if ever, ask you to provide sensitive data like this via email. If you receive such a request via email and you are even the slightest bit unsure or suspicious, the proper and safe course of action is always to separately contact the organization directly. Use a trusted phone number that you find on their official website (do not use a number provided in the email itself!) or navigate directly to their official website yourself by typing the address directly into your web browser – do not click links in the email.
By taking the time to genuinely understand the threat landscape inherent in email communication, familiarizing yourself with how free email lookup tools work (and importantly, their limitations), and committing to applying the verification techniques we’ve outlined, you are now significantly better equipped to navigate the online world more safely and responsibly. Remember to always use these kinds of resources ethically, prioritizing respect for people’s privacy and always adhering to legal guidelines in your location regarding data use.
As someone who has spent a good amount of time immersed in the world of online investigation and security best practices, my strong advice is this: Stay consistently informed and remain vigilant. The digital environment is constantly changing, and new types of scams unfortunately emerge with discouraging regularity. However, by employing a combination of this kind of knowledge, applying critical thinking to the messages you receive, and taking a proactive approach to your online security, you truly empower yourself. You can significantly better protect yourself, and potentially help others, from the ever-present and evolving threat of online fraud.